nginx lua防火墙防SQL注入配置
|
admin 2025年6月28日 22:17
本文热度 1086
2025年6月28日 22:17
本文热度 1086
|
一、防火墙配置
参考 nginx配置lua防火墙
二、准备演示环境
1. 前端演示页面
<html>
<head>
<title>登陆</title>
<meta charset="utf-8">
</head>
<body>
<div>
用户名:<input type="text" name="user" id="txtUser"><br>
密码:<input type="password" name="pwd" id="txtPassword"><br>
<input type="button" onclick="login('login')" value="登陆"> <br>
<div id="divMsg"></div>
<script>
function login(action) {
var httpRequest = new XMLHttpRequest()
httpRequest.onreadystatechange = function () {
if (httpRequest.readyState == 4) {
document.getElementById("divMsg").innerText = httpRequest.responseText
}
}
httpRequest.open('POST', `/api/${action}`, true)
httpRequest.setRequestHeader(
'Content-type',
'application/x-www-form-urlencoded'
)
var user = document.getElementById("txtUser").value
var pwd = document.getElementById("txtPassword").value
var str = `username=${user}&password=${pwd}`
httpRequest.send(str)
}
</script>
</div>
</body>
</html>
2. 服务端演示代码,模拟SQL注入
@Autowired
JdbcTemplate jdbcTemplate;
/**
* 拼sql查询
*
* @param user
* @return
*/
@PostMapping("/login")
public String login(User user) {
String sql = "select * from sys_user where user_name = '" + user.getUsername() + "' and pass_word = '" + user.getPassword() + "'";
System.out.println("SQL:");
System.out.println(sql);
List<Map<String, Object>> maps = jdbcTemplate.queryForList(sql);
System.out.println(maps.size());
if (maps.size() > 0) {
return"login success";
} else {
return"login fail";
}
}
3. nginx代理设置
location /api/ {
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header REMOTE-HOST $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://192.168.1.18:8093/;
}
4. 配置拦截参数(lua防火墙通过检测post表单中的关键字实现拦截)。
# 设置SQL注入的关键参数
echo "'\s+or\s+" >> /usr/local/nginx/conf/ngx_lua_waf/wafconf/post
# 重新加载,使配置生效
/usr/local/nginx/sbin/nginx -s reload
三、效果演示
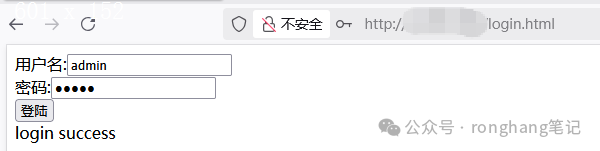
1. 正常登陆
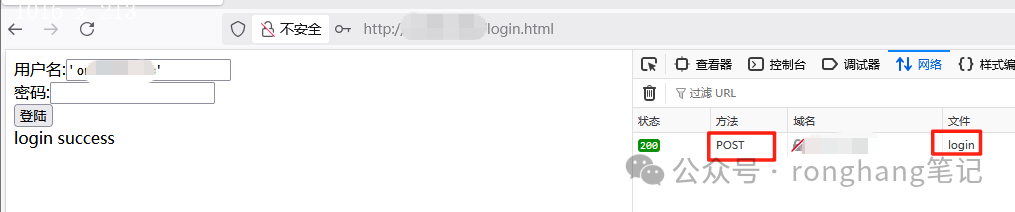
2. 注入成功,在配置post拦截参数以前的效果
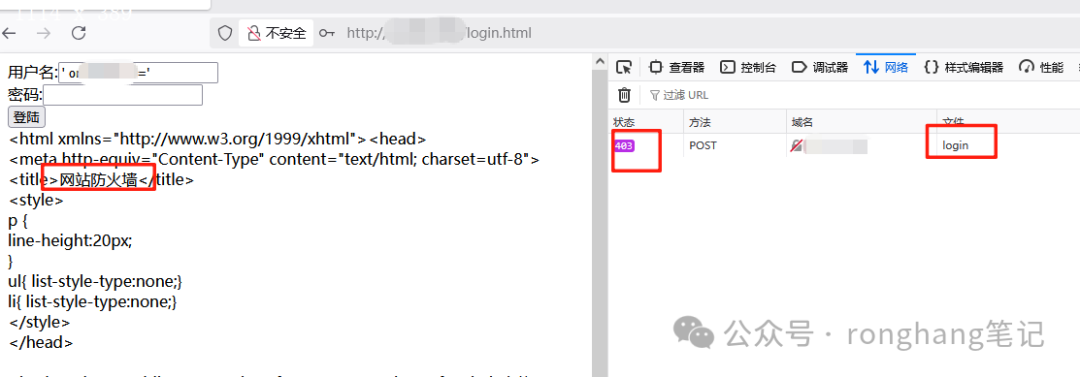
3. 注入被拦截,在配置post拦截参数以后的效果
阅读原文:原文链接
该文章在 2025/7/1 23:48:34 编辑过